Alleged Android Version To Break Multiple Root Apps
Recently, a new set of commits have been unveiled by the Android Open Source Project in order to enhance the security aspect of the platform against future malicious attacks. While the improvement was meant to protect users and their smart devices, it appears that the new feature will also eliminate various root apps available for root devices.
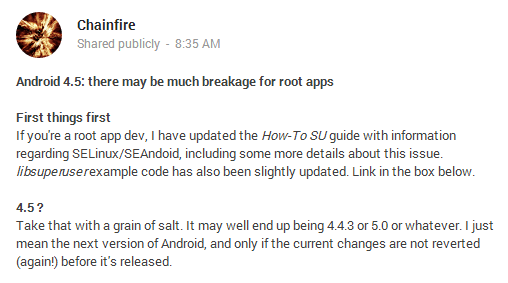
Chainfire, the developer of one of the most well known root access management apps available, the SuperSU app, has revealed the purpose and the effect of all those code changes. He released a couple of ideas regarding the future Android version which is scheduled for release, in order to alter other root app developers, and maybe even Google developers, as well.
As far as the code is concerned, the security issues use SELinux, a feature introduced along with the Android 4.3 firmware, in order to prevent various files under the /data partition from being executed using an unconfirmed domain tag. The connection with the root apps is that the security feature is making use of the same mechanism used by different apps to work on a rooted device.
Bottom line, if the security patch will be a part of the actual Android update somewhere in the future, most of our beloved root apps will no longer work. However, it is worth mentioning the fact that this is not definitive. Perhaps, Android developers will change the code somehow before an official release appears, and after the hard work of app developers, we will be still enjoying our favorite root apps.
Most likely is if this update manages to see the light of the day, many apps developers will be quite disappointed. As most of the root apps we are currently using will not work on the next Android firmware, it will definitely become a big problem. So far, all we have to do is to hope that this is only a rumor and the Android developers will use something else in order to protect their platform from malicious attacks and bugs.